Tech
How To Detect A BlackLotus UEFI Bootkit Infection – Microsoft
(CTN NEWS) – Microsoft has provided instructions to assist organisations in determining whether hackers used the CVE-2022-21894 vulnerability to compromise or target computers with the BlackLotus UEFI bootkit.
Microsoft’s recommendations can be used by both organisations and people to recover from an attack and stop threat actors utilising BlackLotus from becoming persistent and evading discovery.
Since last year, BlackLotus has been promoted on hacking forums as a piece of malware that can disable different security mechanisms (such as Defender, HVCI, and BitLocker) and avoid antivirus detection.
A licence cost $5,000, and rebuilds could be purchased for $200.
Early in March, experts at the antivirus firm ESET confirmed the malware’s capabilities and reported that it performed as promised.
Identifying BlackLotus Infection Clues
The Unified Extensible Firmware Interface (UEFI) malware is particularly difficult to detect because it may be deployed early in the boot process to disable security safeguards, running before the operating system.
It can be particularly difficult to identify malware for the UEFI (Unified Extensible Firmware Interface), as this threat operates before the operating system boots up, allowing it to launch payloads early in the boot process to disable security protections.
The Microsoft Incident Response team examined machines infected with BlackLotus and discovered many stages throughout the malware’s installation and operation that may be monitored for its detection.
According to the researchers, in order to identify a BlackLotus UEFI bootkit infection, defences should seek for the following artefacts:
- Recently created and locked bootloader files
- Presence of a staging directory used during the BlackLotus install in the EPS:/ filesystem
- Registry key modification for the Hypervisor-protected Code Integrity (HVCI)
- Network logs
- Boot configuration logs
Boot Partition Artifacts
BlackLotus will lock the EFI system partition, commonly known as ESP, in order to prevent their deletion or alteration because it needs to write malicious bootloader files there.
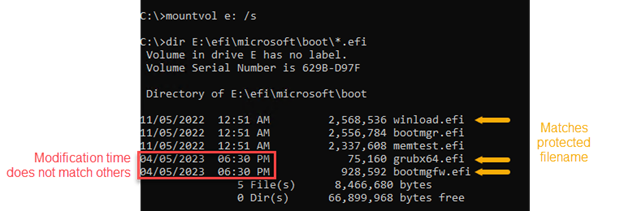
In the ESP location, recently modified and locked files, especially if their names coincide with those of known BlackLotus bootloader files, “should be considered highly suspect.”
Disconnecting the devices from the network and searching them for any indications of BlackLotus-related activity is advised.
Microsoft advises mounting the boot disc and checking the creation dates of the files with inconsistent creation times using the mountvol command-line tool.
Using the following command on a Command Prompt with Administrator rights, you can mount the ESP partition:
mountvol[available drive letter] /s
For instance, you can run the following command if the G: drive letter is available:
mountvol g: /s
Threat hunters can attempt to determine the bootloader file’s hash if the modification time does not appear suspicious. A file access error should be the result on a hacked device because BlackLotus locks files to prevent tampering.
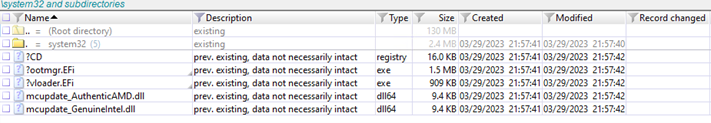
The “/system32/” directory on the ESP, which serves as a storage area for the files necessary to install the UEFI virus, is another indication that BlackLotus is present.
According to Microsoft, a successful installation of BlackLotus causes the files inside “ESP:/system32/” to be deleted, but the directory is left in place. This can be used by forensic analysts to look for the deleted files.
Network Clues, Registry Entries, And Logs
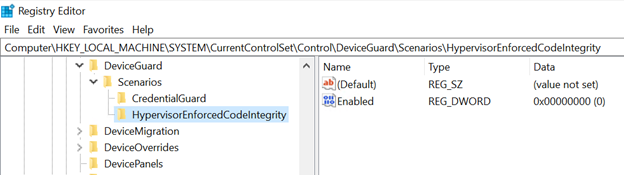
Disabling the hypervisor-protected code integrity (HVCI), which enables BlackLotus to load unsigned kernel code, is one of its capabilities.
To do this, modify the HVCI registry key’s Enabled value to 0 (zero), as shown in the figure below.
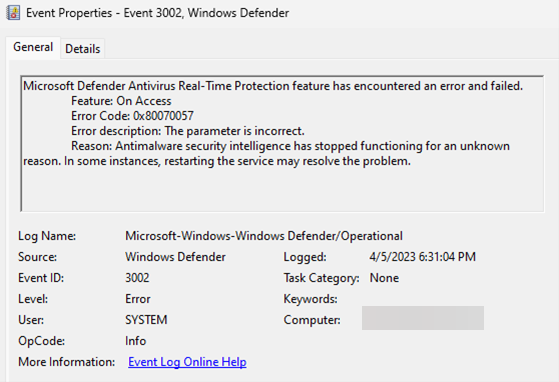
Microsoft Defender Antivirus, the standard security programme for Windows, is a further security component that BlackLotus disables.
The Microsoft-Windows-Windows Defender/Operational Log may contain an entry as a result of this action in the Windows Event Logs.
In the event that Defender is turned off and the service terminates suddenly, an Event ID 7023 may also be recorded in the System event log.
Threat hunters are advised by Microsoft investigators to check network logs for connections coming from winlogon.exe on port 80, which may be a sign that BlackLotus is attempting to connect to its command and control (C2) server.
- “This is the result of the injected HTTP downloader function of BlackLotus connecting to the C2 server or performing network configuration discovery” – Microsoft
The boot configuration logs, also known as MeasuredBoot logs, which provide information about the Windows boot process, may contain additional proof of BlackLotus compromise.
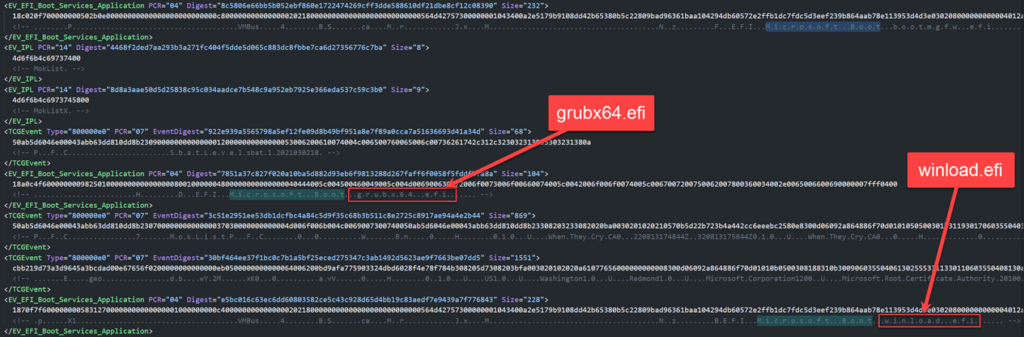
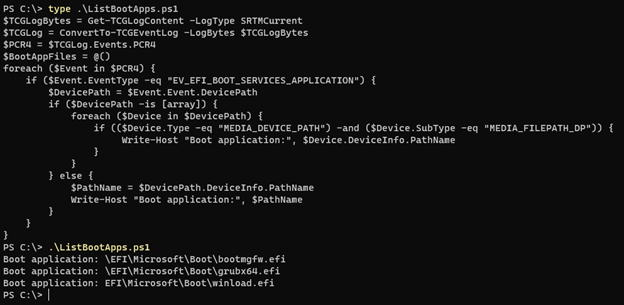
Two boot drivers—grubx64.efi and winload.efi—become accessible when the bootkit is activated. Analysts can identify the parts that have been added to or removed from each machine boot by comparing the logs for each system reboot.
Microsoft cautions that utilising a forensic image or raw NTFS reading tool may make it easy to view the MeasuredBoot log files.
After decoding and converting the data to an XML or JSON file format, it can be read. For parsing and retrieving the logs, Microsoft provides a sample script based on the free software TCGLogTools.
Here is an illustration of the BlackLotus drivers that the test script displayed on an infected computer:
Preventing The Breach Of BlackLotus
In order to clear a machine after a BlackLotus infection, it must be disconnected from the network and either restored from a clean backup with an EFI partition or reinstalled with a clean operating system.
Defenders can avert a compromise by spotting an intrusion before the adversary may utilise UEFI malware, even though post-infection artefacts are useful in identifying the sort of malware used.
However, in order to launch a UEFI bootkit, the target computer must have privileged access, either remotely or physically. As a result, a first-stage threat and an initial access vector come before the persistent infection.
Microsoft advises organisations to adhere to the principle of least privilege and maintain good credential hygiene in order to prevent an infection from BlackLotus or other malware that exploits CVE-2022-21894 in their systems.
- Avoid using admin-level service accounts that are domain-wide. Restricting local administrative rights can prevent the installation of undesirable programmes and remote access trojans (RATs). : Microsoft
Organisations can lower the danger of an adversary acquiring access to or administrative privilege in the environment by installing numerous levels of security controls, or “defence in depth” tactics.
As a result, a BlackLotus attack can be effectively stopped in its early phases before the threat actor can steal the credentials for a user or service account and utilise that information to roam across the network and elevate their privileges.
RELATED CTN NEWS:
iPhone 15 Pro To Feature Conventional Physical Buttons Due To Technical Issues
What Is A Wash Sale And How Does It Impact Your Investments?
Download And Install Samsung Internet Browser APK Latest Version 20.0.6.5