Tech
How To Prevent Stolen iPhone Data Hacking Using Apple Recovery Key?

Apple Recovery Key – While it may seem unlikely that burglars would take your iPhone and your passcode, it has been on the rise recently.
The icing on the cake is that, if you don’t take some preventative measures, you can find yourself locked out of your Apple ID account with little to no means to get back in.
If you own an iPhone, it’s likely that you haven’t given much thought to what you’ll do if it is stolen or lost.
Even less so if you consistently pay for AppleCare+, a protection plan that is meant to give you comfort for as long as you permit the business to charge you for it.
Apple products, which made up eight of the top 10 best-selling cellphones last year, offer a severe security concern when used in public places, as evidenced by the recent spike in iPhone thefts in the US and elsewhere.
Recently, thieves have discovered that the passcode you use to access your smartphone is the most potent tool they can use to bypass all other security measures in place and that once they have it, there isn’t much you can do to stop them.
In a Wall Street Journal article, Greg Frasca, an iPhone user who has been locked out of his Apple account since October, is used as an example.
After spotting the 46-year-old use his passcode in a Chicago bar, the burglars took his iPhone 14 Pro. As a result, they were able to modify his Apple ID password and turn on a little-known security measure called the “recovery key.”
Apple Recovery Key
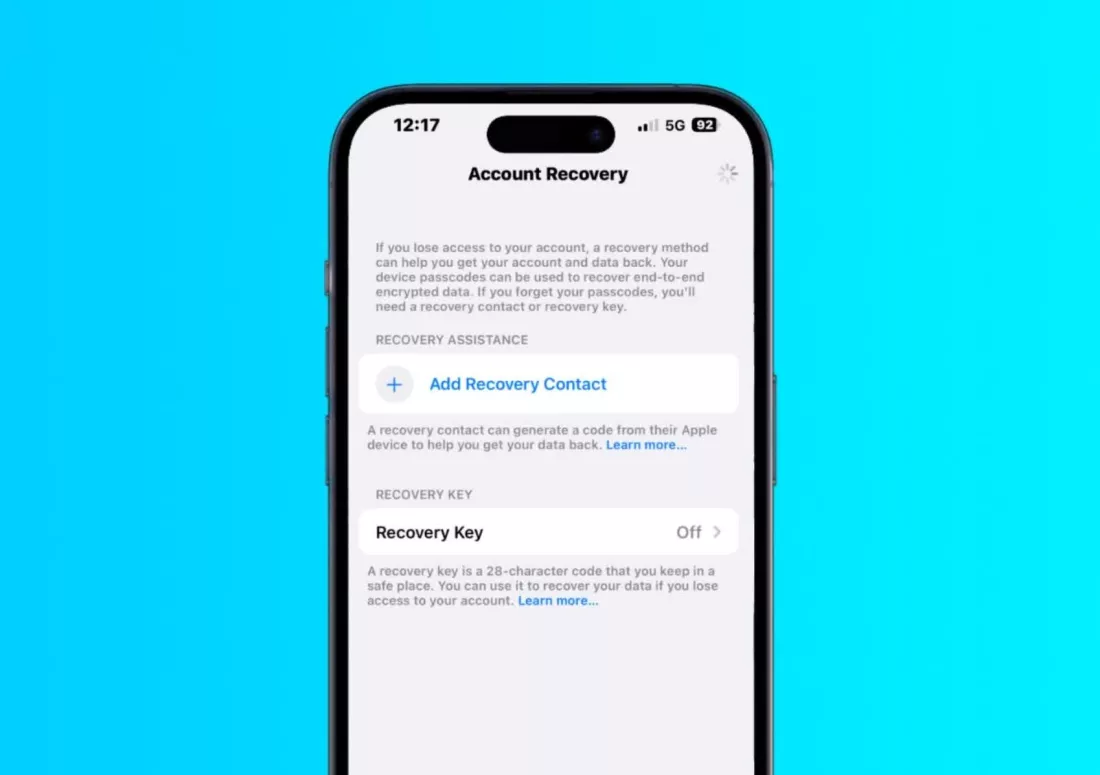
The Cupertino company added the Apple Recovery Key as an optional feature in 2020 to give another level of security against hackers.
In essence, it’s a 28-character code that was produced at random that you can use to stop them from changing your Apple ID password.
Few people use it because the relevant setting is hidden behind numerous others and missing it can prevent you from using any of the devices connected to your Apple ID.
It’s true that in some rare instances where Face ID or Touch ID fail to function for whatever reason, thieves are able to memorise or record the victim typing their passcode.
Still, the only way to get Apple to unlock your account after burglars lock you out of it requires, at most, travelling to Apple’s headquarters in person or mailing a $10,000 cheque.
If you’re lucky, the business will typically only assist you if you supply the Apple Recovery Key.
So what can you do to make sure that this never occurs to you? One way to reduce the likelihood that criminals will be able to recall your passcode is to solely use Face ID or Touch ID.
Another option is to create a bespoke alphanumeric code.
Under Settings -> Face ID & Passcode (Touch ID & Passcode on iPhone SE/8/older) -> Change Passcode, you can accomplish this.
Utilising the Screen Time feature, which is typically utilized for parental control, is an additional option.
Set up a different key from the one you use for your phone’s passcode by going to Settings -> Screen Time -> Use Screen Time Passcode.
Then, on the same settings page, navigate to Content & Privacy Restrictions and turn it on using the toggle. Finally, pick “Don’t Allow” for Account Changes under the “Allow Changes” category by swiping down the list.
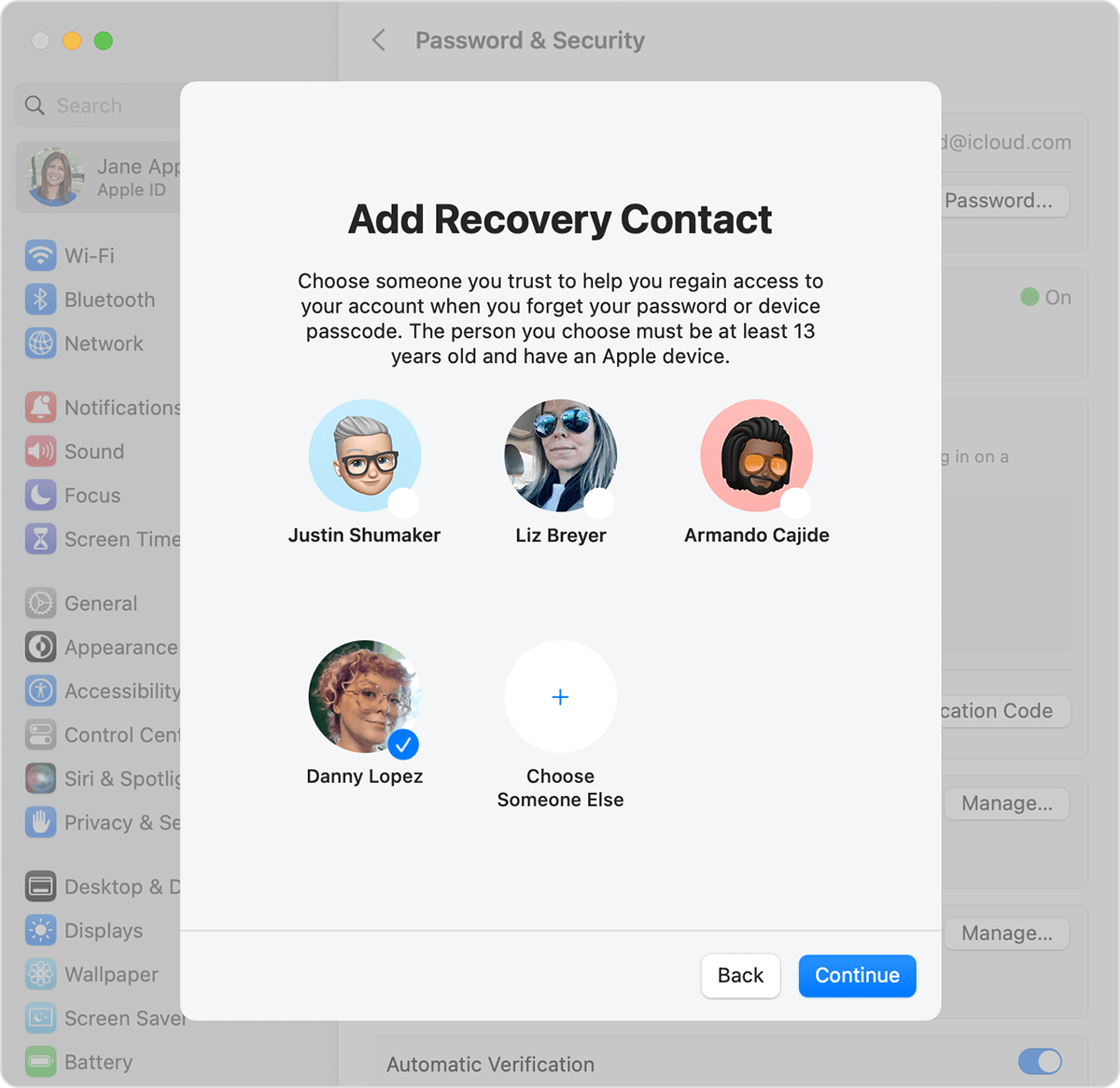
By navigating to Settings -> Your Name -> Password & Security -> Account Recovery and adding a person you want to be able to aid in case you require recovery assistance.
You may create a recovery contact if you want to be completely thorough.
Additionally, it’s a good idea to establish a routine for frequently creating offline backups of your critical files.
As for Apple, it responded to the revelation in a customary manner, telling consumers that it takes every security breach “very seriously, no matter how rare” and that it is “always investigating additional protections against emerging threats like this one.”
Although they’re far from ideal, other organisations like LinkedIn and Uber already use additional methods of identity verification that can assist with account recovery among other things.
But the IT sector hasn’t yet figured out a decent method to strike a balance between practicality and security without violating your privacy with features like face recognition or mandating a government-issued ID for account protection.
RELATED CTN NEWS:
What is a Stylus Pen? Types And How Do Stylus Pens Work?
NVIDIA Reflex: How To Enable Nvidia Reflex In 2023?
Google Pixel 7 vs. Pixel 7 Pro: Which One Is The Best?