Tech
DevSecOps: Debunking Common Myths about DevSecOps
In a rapidly evolving business landscape, it is essential to incorporate cutting-edge technologies over time. While many organizations have switched to DevSecOps for better security, some remain skeptical due to common preconceived notions associated with it. It involves integrating security seamlessly into every stage of the software development life cycle (SDLC).
However, like any tech initiative, it harbors its share of misconceptions. To embark successfully on a DevSecOps journey, it is crucial to debunk these myths.
Before diving into the myths, let’s understand DevSecOps in more detail.
What Is DevSecOps?
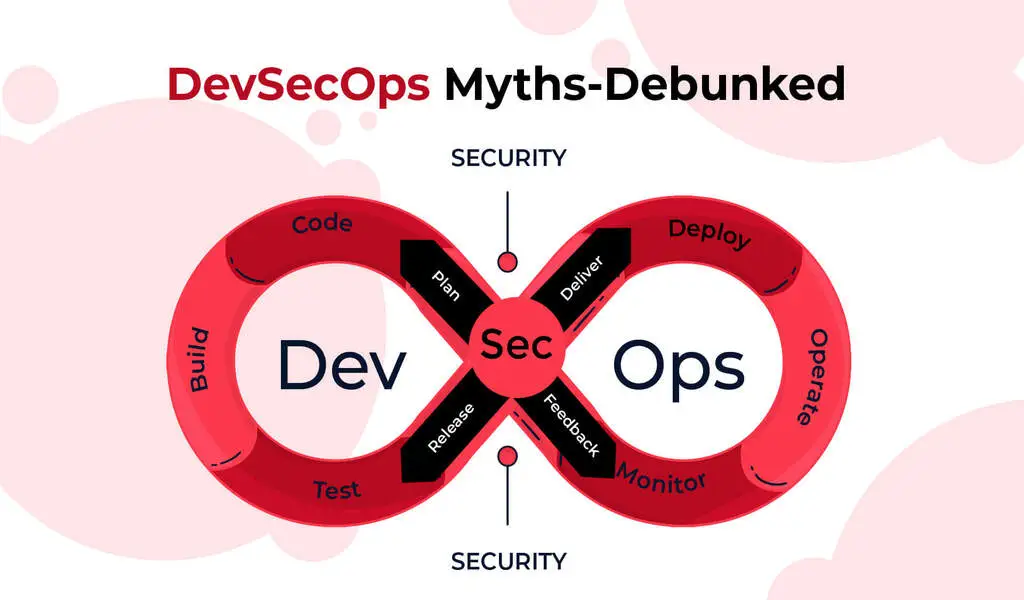
DevSecOps aligns closely with traditional DevOps, emphasizing the integration of cross-functional teams collaborating to facilitate secure, continuous software delivery.
The DevSecOps development lifecycle is an iterative process commencing with code creation, followed by build initiation, deployment to the production environment, and continuous runtime monitoring, with security seamlessly woven into every stage of this cycle.
7 Features of DevSecOps
Once you sign up for DevSecOps services, you will get access to the following features to reap benefits from:
Security Awareness & Ownership: Everyone involved in DevSecOps should grasp security fundamentals and take ownership, making security everyone’s responsibility.
Automated Operation: Security tools must automate testing without manual steps, configurations, or slowdowns, aligning with CI/CD automation.
Fast Results: Security tooling should deliver near-real-time results to match the speed of modern DevOps.
Broad Scope: Security tools must cover diverse environments (containers, serverless, etc.) and application types (open-source, third-party).
Shift-Left & Shift-Right: Assess security early (“shift-left”) and in production (“shift-right”) due to attack prevalence and varied scenarios.
Accuracy: Automation is essential, but results must be accurate and avoid false positives/negatives to aid remediation.
Developer Acceptance: The entire DevSecOps process, tools, and practices must gain acceptance from developers, testers, and security teams for effectiveness.
5 DevSecOps Myths- Debunked!
We have compiled a list of myths related to DevSecOps and provided an in-depth explanation for each of them:
Myth 1: DevSecOps Results in a Loss of Control
Some see security as a stifling force that curbs creativity. DevSecOps automation may also raise concerns about job roles. To counter this, educate your team on the process’s benefits. Share real-world success stories from organizations that have harnessed DevSecOps to bolster collaboration and efficiency.
Myth 2: DevSecOps Can Be Purchased and Deployed
DevSecOps is not a one-size-fits-all product. It is a philosophy that necessitates cultural change, collaboration, and process adaptation. Beware of vendors promoting it as an off-the-shelf solution. Awareness is key; make it clear that DevSecOps is a cultural shift, not a product purchase.
Myth 3: DevSecOps Is a Set-and-Forget Model
DevSecOps is not a static solution. It is adaptable and meant to align with your organization’s unique goals and culture. While automation is pivotal, human input remains essential for ongoing success. Change is a constant; prepare to adapt as needed.
Myth 4: DevSecOps Only Alters Development, Not Security
DevSecOps involves security teams collaborating closely with developers and operations. It is not about dictating terms but sharing goals to find the best solutions. Security practices may need adjustment. Education is the bridge to dispel this myth.
Myth 5: DevSecOps Is Solely Technological or Cultural
DevSecOps isn’t just a tech initiative or a cultural shift—it is both. Technology plays a significant role, but collaboration, culture, and mindset are equally vital. The key lies in balancing these elements for successful DevSecOps implementation.
Holistic Security Integration
Integrating security comprehensively throughout your software delivery solution is the key to instilling security from inception to deployment. Bid farewell to prolonged security audits that disrupt development and productivity. Advanced DevSecOps automates security and compliance testing, ensuring the use of approved components.
End-to-end automation minimizes the introduction of security flaws due to human errors. Any issues that arise can be swiftly identified and rectified before compromising code reaches deployment. Automation also governs access controls, overseeing alterations and safeguarding critical components against inadvertent changes.
Breaking Down Silos with a Unified Pipeline
A shared pipeline platform spanning development, quality assurance, and operations provides advanced control and visibility across the entire development process. This holistic approach grants security, development, and operations teams a comprehensive understanding of the digital ecosystem, facilitating informed innovation.
A shared pipeline identifies problematic code before release, allowing incremental fixes instead of post-deployment patching. Enhanced visibility fosters better communication, reducing blame and encouraging collaboration.
Empowering Progressive Delivery
End-to-end software delivery solutions enable progressive software releases, accelerating secure deployments. Progressive delivery introduces new code incrementally, steering clear of disruptive “big bang” releases.
This approach minimizes risk by testing code on a small scale and swiftly addressing any issues that arise, all while retaining trusted governance. An “enterprise kill switch” stands ready to respond to critical production incidents.
Progressive delivery nurtures innovation by providing developers a low-risk environment to experiment and create. It harmonizes the needs of development and InfoSec, resulting in faster time-to-market for products.
All in All
In the world of DevSecOps, dispelling myths and fostering a deep understanding of its essence is paramount. It is not just about security; it is about a holistic transformation that merges technology, culture, and collaboration to enhance your development and security processes.





























